
Secret Mail uses digital passports to replace the traditional account password mode, which naturally prevents man-in-the-middle attacks, client risks, phishing attacks, etc

秘邮-探秘版

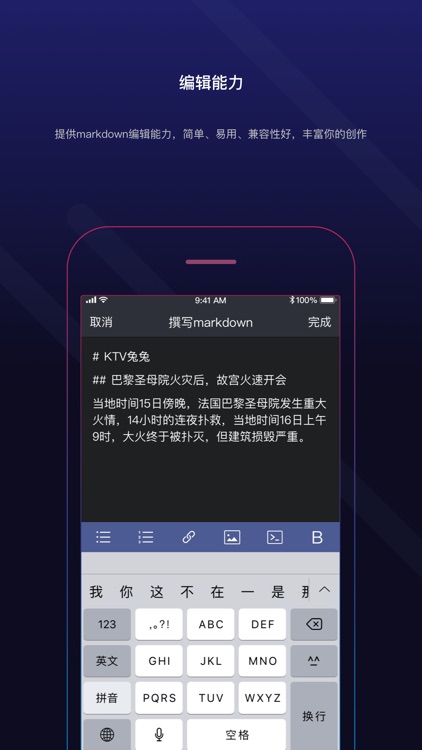
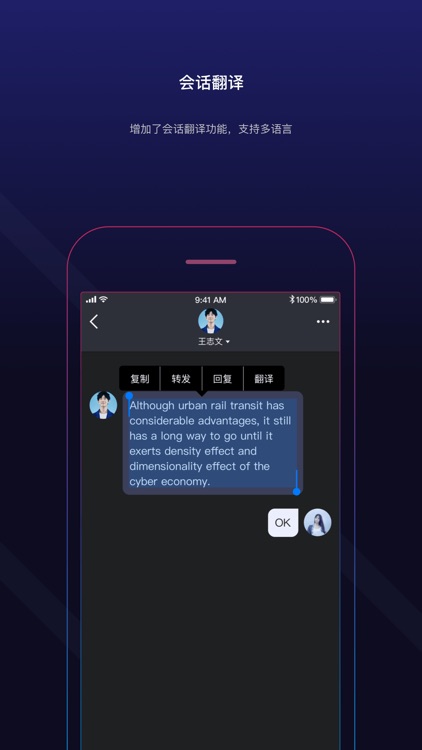
What is it about?
Secret Mail uses digital passports to replace the traditional account password mode, which naturally prevents man-in-the-middle attacks, client risks, phishing attacks, etc., to protect digital assets and establish a more secure, autonomous and credible account system.

App Screenshots




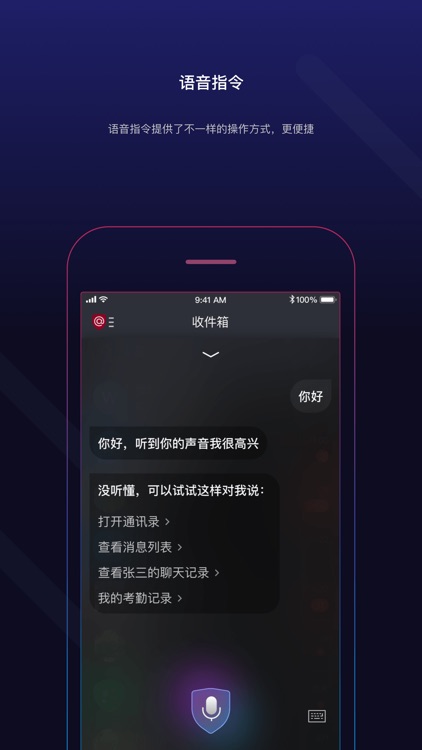
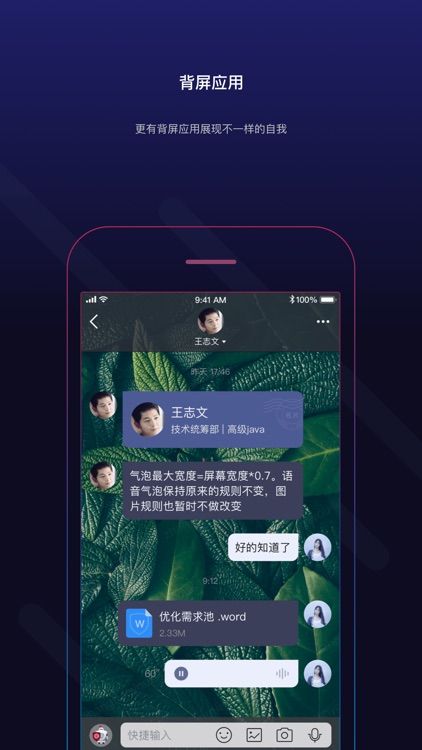
App Store Description
Secret Mail uses digital passports to replace the traditional account password mode, which naturally prevents man-in-the-middle attacks, client risks, phishing attacks, etc., to protect digital assets and establish a more secure, autonomous and credible account system.
The secret mail adopts the mailbox addressing mode, so that you and the world can contact at any time to communicate seamlessly with users of existing mailboxes.
The secret mail provides end-to-end encrypted message communication and real-time communication capabilities. When the client sends the information, the data is completely encrypted, free from the dependence on the channel encryption, realizing true private communication, so that the communication cannot be intercepted, intercepted, or forged. .
Strictly protect the privacy and security of users' identity, information, relationships and rights. We do not store any personal information other than those required by laws and regulations. Users cannot search by search, and your information is completely self-controlled.
Through privacy cloud and client end-to-end encrypted storage, high security data hosting, trusted security, so that all data can be stored privately and safely.
By inviting friends to create your own social circle, record your life and share each wonderful moment with your friends, encrypt the information in the group, and ensure that group messages are not leaked; enterprises can use the collaborative group management team to encrypt information, store documents, and realize information and Strong team collaboration capabilities such as secure sharing of documents; a large group of up to a million people can be formed to achieve anonymized socialization through custom identity. The group also supports the ability to post, reply, top, and group topics to achieve powerful functions in different scenarios.
The topic is flexible and fast group chat. Any content can be set as a topic and sent to a designated group of people. The participants can quickly respond to the topic by “reply”, and the group can also establish a topic to realize private chat within the group. Internal activity organization, etc.
The intelligent scene assistant provides customized assistant services according to different interaction objects such as people, groups, topics, applications, and the Internet of Things. The user establishes flexible and personalized shortcuts through customization.
What is a blockchain mailbox?
Blockchain mailbox features: Bind the email address and the public ID's identity ID, and use the public and private key encryption and verification methods to give the mailbox three new core features: autonomy, security, and trustworthiness.
1. Power autonomy (determination of authority) The use of each user's full use of the private key's use of power to ensure the self-holding of information generation, acquisition and storage 1. When the information is generated, each information passes the private key and signature. To determine the legitimacy of the sender of the message 2. Acquire: The sent message is encrypted with the other party's public key to ensure that it can only be unlocked by the other party's private key, ensuring the recipient's information security and the information holder's right to confirm ( My information is only my responsibility, my information can only be read.) 3. Because it is private key encryption and integrity check, to ensure that information is stored anywhere, even if it is cloud storage, it will not be stolen, stolen or hijacked.
Second, open secure storage (open and private) 1, can ensure that data is stored at either end, because public and private key encryption can be stored anywhere under the conditions of secure storage
Third, the trusted mechanism We use the public key as the ID of the identity, each email address is bundled with a unique public key, through the verification mechanism, the identity of the sender can be completely determined.
AppAdvice does not own this application and only provides images and links contained in the iTunes Search API, to help our users find the best apps to download. If you are the developer of this app and would like your information removed, please send a request to takedown@appadvice.com and your information will be removed.