
Telmalink® was designed and created with the main objective to help its users to secure their private data, using the safest encryption algorithms in the world, and to be able to share this data with their contacts in a secure environment

Telmalink

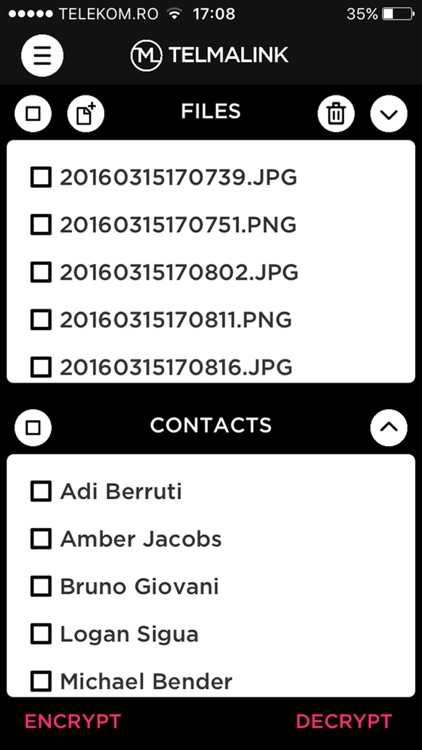
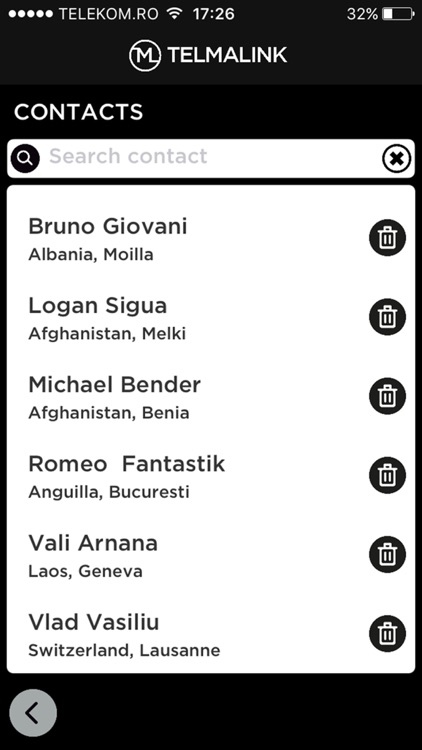
What is it about?
Telmalink® was designed and created with the main objective to help its users to secure their private data, using the safest encryption algorithms in the world, and to be able to share this data with their contacts in a secure environment.

App Screenshots


App Store Description
Telmalink® was designed and created with the main objective to help its users to secure their private data, using the safest encryption algorithms in the world, and to be able to share this data with their contacts in a secure environment.
From now on, Telmalink® ensures communication between financial institutions and customers, clinics and patients, lawyers and clients, producers and distributors, companies and their employees… between you and others who care about privacy on the Internet. You don’t need to be an expert to encrypt your data: the program does it for you.
Telmalink® has been developed entirely in Switzerland. Our team of cryptographers and programmers, our servers and offices are located in Geneva. Telmalink® is a Swiss made product now available to the world.
In order to achieve the above objectives, Telmalink® offers its community state-of-the-art encryption capabilities by using a double symmetric encryption mechanism, AES and Serpent. Moreover, Telmalink® uses a public-key cryptography, also known as asymmetric cryptography. It is a class of cryptographic protocols based on algorithms that require two separate keys, one of which is private, and the other is public. Although different, the two parts of this key pair are mathematically linked.
What is AES? It stands for Advanced Encryption Standard and it’s one of the most secure encryption algorithms in the world. This algorithm became really popular due to the fact that the US government is using it to protect classified information. AES is one of the cryptographic algorithms used by NSA's Information Assurance Directorate in technology, approved for protecting national security systems.
What is Serpent? Another finalist in the Advanced Encryption Standards contest. This algorithm is a 32-round substitution-permutation network operating on a block of four 32-bit words. Each round applies one of eight 4-bit to 4-bit S-boxes 32 times in parallel. Serpent was designed so that all operations can be executed in parallel, using 32 bit slices.
Both AES and Serpent are symmetric-key algorithms because they use the same cryptographic keys for both encryption of plain text and decryption of cipher text. In Telmalink® the symmetric encryption is used for encoding client’s data (files).
In order to facilitate its users to share the encrypted data in a secure way, Telmalink® is using the 25519 elliptic curve for sharing the encryption keys between users. In this way, the sender is encrypting the keys used for AES and Serpent using the public key of the receiver, only with the correct private key, decryption can be done.
AppAdvice does not own this application and only provides images and links contained in the iTunes Search API, to help our users find the best apps to download. If you are the developer of this app and would like your information removed, please send a request to takedown@appadvice.com and your information will be removed.